https mod_ssl协议加密
httpd-2.2.3-43.el5.i386.rpm httpd的主要
httpd-devel-2.2.3-43.el5.i386.rpm 关于开发的包(可以不装)
httpd-manual-2.2.3-43.el5.i386.rpm httpd的手册
Apache 的主根/etc/httpd
(1)目录安全性
主配置文档 /etc/httpd/conf/httpd.conf
Keepalive off 可以打开(一次连接多次请求)
Maxkeepaliverequest 15 最大连接请求
父进程处理用户请求:
1.每来一个用户请求,父进程就派生一个子进程去处理用户请求
2.父进程保持几个空闲的子进程
模块:
<IfModule prefork.c> 判断是否有该模块,有就执行中间内容,没有就判断下一个模块
StartServers 8 中间子进程数
MinSpareServers 5 最少空闲子进程
MaxSpareServers 20 最多空闲子进程
ServerLimit 256 同时在线用户数量
MaxClients 256 可以根据用户访问数量,性能来调
MaxRequestsPerChild 4000 每个子进程可以接受的请求后便终止掉,同时可释放内存垃圾
</IfModule>
Listen 80 监听端口
Listen 800 创建基于虚拟主机的监听端口
LoadModule 后面是可以动态调用的模块
User apache 运行apache的用户
Group apache 运行apache的用户组
UseCanonicalName Off 做虚拟主机就为off
DocumentRoot "/var/www/html" 默认该站点的主目录
目录安全性,实现站点得安全
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
保证基本站点的安全性:
<Directory "/var/www/html">
Options Indexes FollowSymLinks 选项indexes 目录浏览属性,主页没人内容时可以看到主目录的一些文件 fllowsymlinks 在主目录中可以防止符号链接进行跳转
AllowOverride None 身份验证(all) AllowOverride all
Order allow,deny 先看deny,再看allow
Allow from all 允许访问的主机(可以设定某个ip)
</Directory>
Allow from all
</Directory>
做身份验证
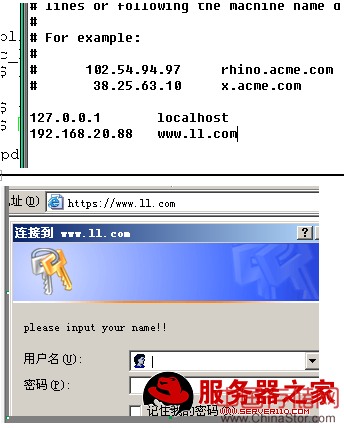
编译一个文件:/var/www/html/.htaccess(身份验证的说明)
authuserfile /var/www/html/.httpasswd (验证时的账号文件,取名可随意)
authtype basic (验证类型为基本)
authname “plesae input your name” 交互文字
require valid-user (有效的账号来访问,或者直接指定某个用户)
创建账号文件:
htpasswd -c /var/www/html/.httpasswd user1(认可的账户) -c表示创建一个新的
Httpd -l 可以查看httpd的模块 访问日志 /var/log/httpd------>/etc/httpd/log
/var/www/html 基本站点
/etc/httpd/run 记录apache在运行时状态参数
/etc/httpd/run/httpd.pid 记录apache服务器运行时进程的id号(父进程号)
Ps -aux 查询所有进程 父进程不会为用户服务,子进程为用户服务 父进程管理子进程
(2)证书安全性
一、利用windows2008做ca< XMLNAMESPACE PREFIX ="O" />
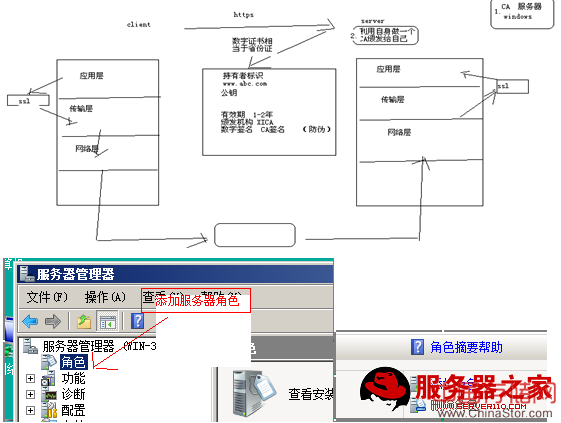
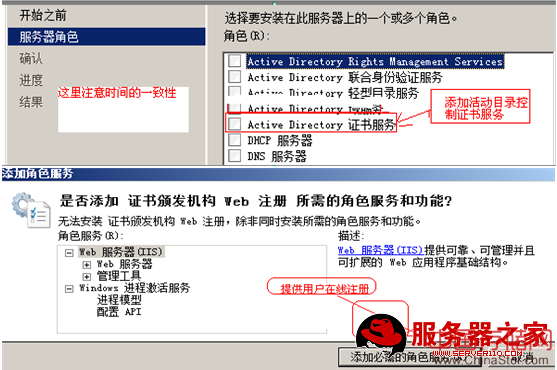
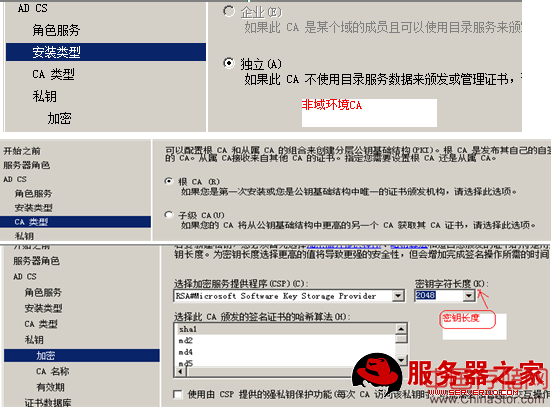
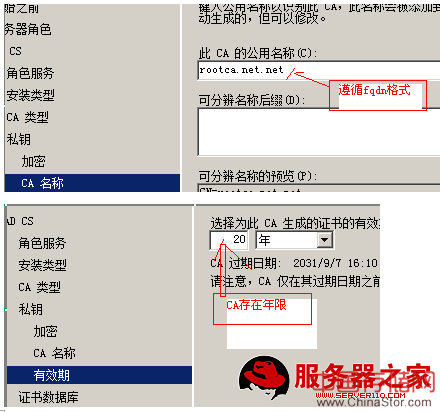
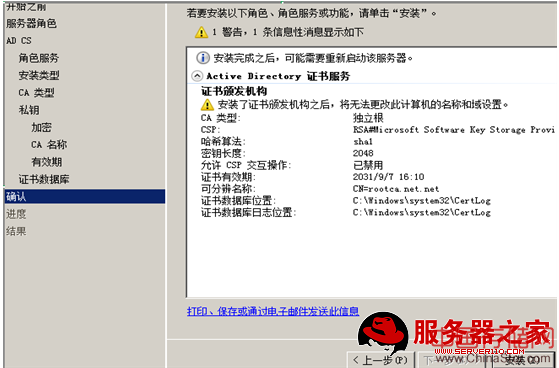

此时CA服务器器已经做好
CA客户端得像CA服务器做一个请求,使用一个工具openssl,用这个工具产生一个请求文件
[[email protected] ~]# cd /etc/httpd/
[[email protected] httpd]# mkdir certs (创建一个目录,存放所有请求文件,钥匙等)
[[email protected] httpd]# cd certs/
先做钥匙,在根据钥匙产生请求文件
[[email protected] certs]# openssl genrsa 1024 (产生非对称加密算法,1024位长度)
Generating RSA private key, 1024 bit long modulus
..............................................++++++
..++++++
e is 65537 (0x10001)
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDImDeuIH3QvvlQJOFHomeSEosRNb6+WbKmkNzkwC9dDr6h2YOp
K9JBM/d+ajQbJy0h94qaRqx6GurJCBCTCwuABEqZAzAUL4N/SmMbNnNGI7kV51C0
2GAIeBIOVMaCE7FUvlIpnGt7kA6hEWXtRPA1pT3NHQMC1Hy6qqDh2P1gjQIDAQAB
AoGAQwJ+jz+xZ/t0A67eRvTcznI9XLlsh+AlCvmXoR8Gc3rKefzUu7201i1K/0Lx
NyTmMdOkzJbRZVT6m7+C8ewdocWrkvlsZpq+eZWqCLFghDBTbSObLBFpD45L/bvb
j8D94ICWZWzU2QLNHEcQ3CzCP2HWnPrZrXFtDgBv5QiyiGECQQDvZqjtluWlG+m6
Aq1/gLczkEx9bSikoBLgva56MhzxB9julQlyUnuto7nFJ8Rhr1+RlC5NofdH6Y8d
mkxR/JBZAkEA1oC/jrZnIlt3WNaYor04CSz3rvIKFa9d9fTgG2ROKdWVseMa6VlZ
aXYazfFMGboj5O+8MJPHVF8SXp3RoqarVQJBALWax9zr0isM4KGldF27k73+4bdn
/iPb9lYcLeYua7wAOvTJhBAAOCgBgmPoBdYghjvWD8X+bqpTp6hKK0kqcYkCQCUq
O4Zjji0CwgPvcpTHyhy04Nk78IlfUB1cZzP3xh8zdXNT0QbbR0Whg/VouHHAsZVq
ACY+hIvWyR0BpR/UVt0CQQCmPbK1k9pom9PaFK9iBdM9WiOq56GjFnMIU9T+j+9z
oc+MO+YEh2lFZxriy3IE2bcAeKayESTfHbDlHfFIGMu0
-----END RSA PRIVATE KEY----- (产生了私钥,但是里面包含公钥)
[[email protected] certs]# openssl genrsa 1024 >httpd.key (产生钥匙文件)
Generating RSA private key, 1024 bit long modulus
........++++++
.............................++++++
e is 65537 (0x10001)
[[email protected] certs]# chmod 600 httpd.key (为了安全起见更改钥匙文件的权限)
根据钥匙文件产生一个证书的请求
[[email protected] certs]# openssl req -new -key httpd.key -out httpd.csr 输出请求文件
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:CN 国家
State or Province Name (full name) [Berkshire]:HENAN 省份
Locality Name (eg, city) [Newbury]:ZHENGZHOU 城市
Organization Name (eg, company) [My Company Ltd]:ll 单位名
Organizational Unit Name (eg, section) []:tec 部门名
Common Name (eg, your name or your server's hostname) []:www.ll.com 为哪个服务器申请
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[[email protected] certs]# ll
total 8
-rw-r--r-- 1 root root 643 Sep 8 00:55 httpd.csr 产生了这个请求文件
-rw------- 1 root root 887 Sep 8 00:47 httpd.key
CA客户端把请求文件发给CA
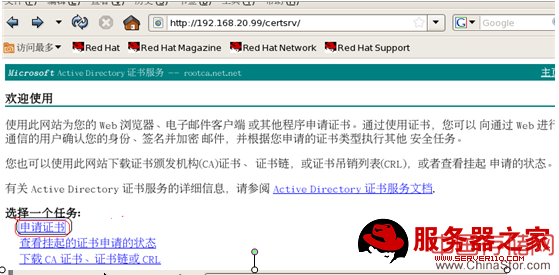
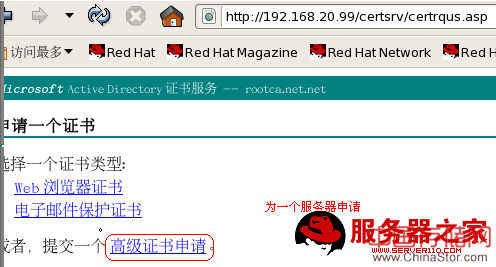
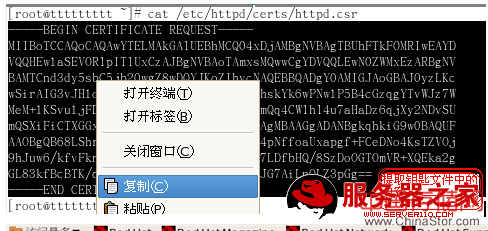
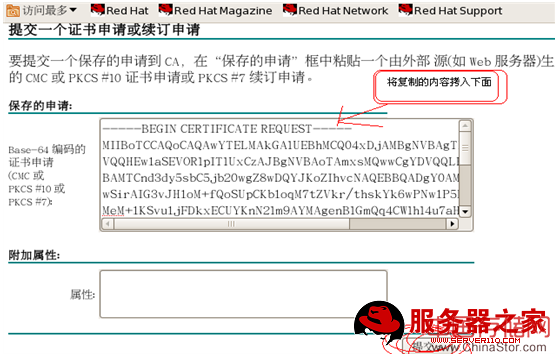
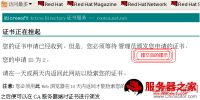
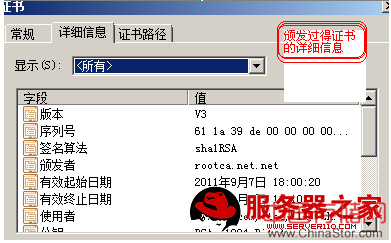
CA客户端证书的下载:
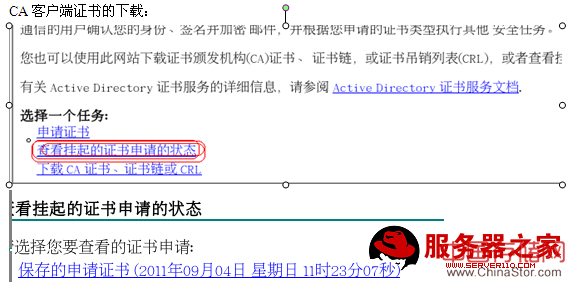
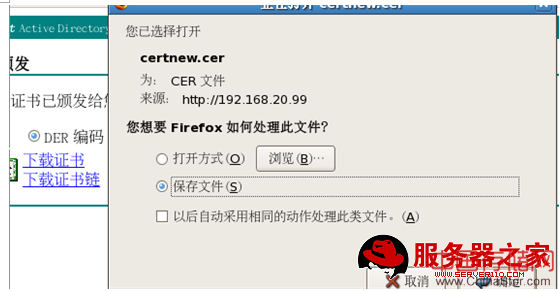
将证书转移:
[email protected] Server]# cd /etc/httpd/certs/
[[email protected] certs]# ll
-rw-r--r-- 1 root root 1016 09-04 11:38 certnew.cer
-rw-r--r-- 1 root root 643 09-04 11:01 httpd.csr
-rw------- 1 root root 891 09-04 11:00 httpd.key
CA客户端证书的安装:
[[email protected] Server]# yum -y install mod_ssl 安装mod_ss包
[[email protected] certs]# vim /etc/httpd/conf.d/ssl.conf 编译mod_ss的配置文件
LoadModule ssl_module modules/mod_ssl.so ssl动态模块
Listen 443 监听端口为443
SSLCertificateFile /etc/httpd/certs/certnew.cer 指明证书文件
SSLCertificateKeyFile /etc/httpd/certs/httpd.key 指明证书对应密钥文件
然后重启http服务
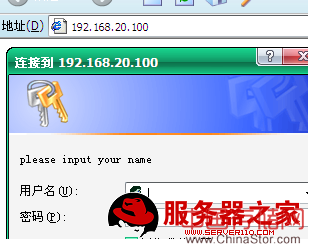
在www服务器客户端访问这个接受过证书的CA证书的www服务器时,将服务器的证书设置为受信任:
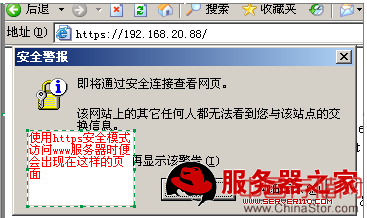
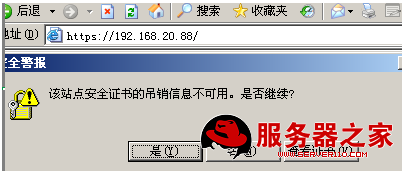
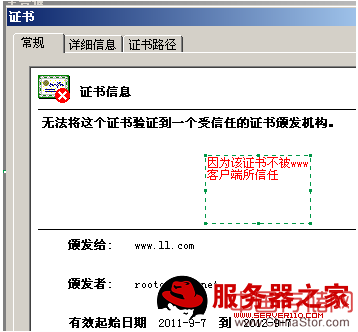
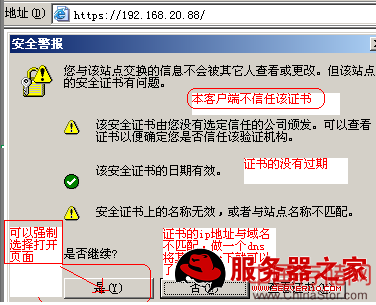
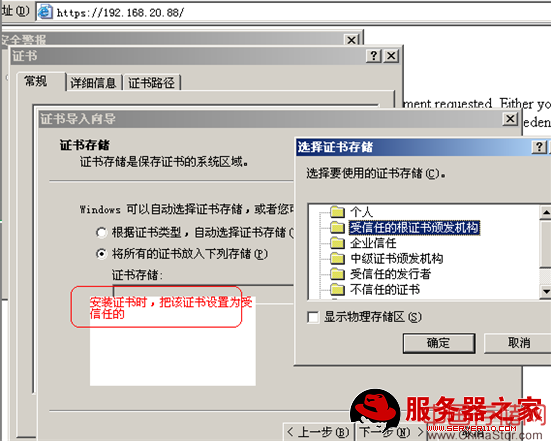
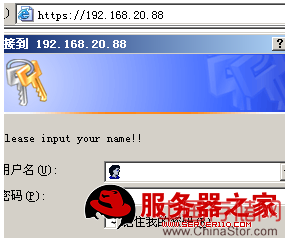
使用linux做CA
自己做自签发的证书:
(1)产生自己的私钥并指明CA的目录
[[email protected] ~]# cd /etc/pki/CA/ 切换待CA目录下
[[email protected] CA]# ll
drwx------ 2 root root 4096 2010-03-12 private
[[email protected] CA]# openssl genrsa 1024 >private/cakey.pem
Generating RSA private key, 1024 bit long modulus
....................................................................................++++++
..................++++++
e is 65537 (0x10001)
[[email protected] CA]# chmod 600 private/* 更改私钥文件的权限
编译[[email protected] ~]# vim /etc/pki/tls/openssl.cnf
45 dir = /etc/pki/CA 指明CA的目录
(2)产生一个自签发的证书(不需要请求文件)
[[email protected] CA]# openssl req -x509 -new -key private/cakey.pem -out cacert.pem -days 3655
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:HENAN
Locality Name (eg, city) [Newbury]:ZHENGZHOU
Organization Name (eg, company) [My Company Ltd]:TT
Organizational Unit Name (eg, section) []:TEC
Common Name (eg, your name or your server's hostname) []:rootca.tt.com
Email Address []:
[[email protected] CA]# ll
-rw-r--r-- 1 root root 1123 09-05 03:09 cacert.pem 产生的证书文件
drwx------ 2 root root 4096 09-05 03:03 private
(3)让CA给服务器颁发证
[[email protected] CA]# cd /etc/httpd/certs/
[[email protected] certs]# opensslgenrsa 1024 >httpd.key
-bash: opensslgenrsa: command not found
You have new mail in /var/spool/mail/root
[[email protected] certs]# openssl genrsa 1024 >httpd.key
Generating RSA private key, 1024 bit long modulus
...++++++
......................................++++++
e is 65537 (0x10001) 产生一个钥匙文件
[[email protected] certs]# openssl req -new -key httpd.key -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:HENAN
Locality Name (eg, city) [Newbury]:ZHENGZHOU
Organization Name (eg, company) [My Company Ltd]:LL
[[email protected] certs]# openssl req -new -key httpd.key -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Country Name (2 letter code) [GB]:CN
State or Province Name (full name) [Berkshire]:HENAN
Locality Name (eg, city) [Newbury]:ZHENGZHOU
Organization Name (eg, company) [My Company Ltd]:TT
Organizational Unit Name (eg, section) []:TEC
Common Name (eg, your name or your server's hostname) []:www.ll.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
产生一个请求
[[email protected] certs]# ll
-rw-r--r-- 1 root root 643 09-05 03:23 httpd.csr 产生的请求文件
-rw-r--r-- 1 root root 887 09-05 03:20 httpd.key 产生的密钥文件
(4)为客户端签发证书
[[email protected] etc]# cd /etc/httpd/certs/
[[email protected] certs]# openssl ca -in httpd.csr -out httpd.crt
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Sep 4 19:50:10 2011 GMT
Not After : Sep 3 19:50:10 2012 GMT
Subject:
countryName = CN 客户端请求的信息
stateOrProvinceName = HENAN
organizationName = TT
organizationalUnitName = TEC
commonName = www.ll.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
B1:0E:57:5F:90:70:1E:6A:EA:CC:C4:8F:BB:AC:47:9C:5E:2B:2A:C6
X509v3 Authority Key Identifier:
keyid:B4:F1:BF:63:BF:B9:73:DD:DF:E7:29:39:D9:01:86:4A:F8:00:64:39
Certificate is to be certified until Sep 3 19:50:10 2012 GMT (365 days)
Sign the certificate? [y/n]:y 是否签发
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[[email protected] certs]# ll
-rw-r--r-- 1 root root 3047 09-05 03:50 httpd.crt 产生它
-rw-r--r-- 1 root root 643 09-05 03:23 httpd.csr
-rw-r--r-- 1 root root 887 09-05 03:20 httpd.key
(5)改变一下主配置,编译/etc/httpd/conf.d/ssl.conf
SSLCertificateFile /etc/httpd/certs/httpd.crt
SSLCertificateKeyFile /etc/httpd/certs/httpd.key
测试语法是否错误,可以使用了httpd -t 然后重启httpd
(6)使用www客户端使得证书被信任
[[email protected] certs]# vim /etc/httpd/conf.d/ssl.conf
131 SSLCertificateChainFile /etc/pki/CA/cacert.pem
SSLCertificateKeyFile /etc/httpd/certs/httpd.key
然后重启httpd
用客户端浏览器打开:
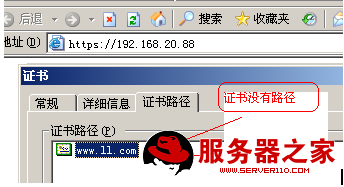
解决办法:
编译 /etc/httpd/conf.d/ssl.conf
SSLCertificateChainFile /etc/pki/CA/cacert.pem 添加路径
然后重启httpd
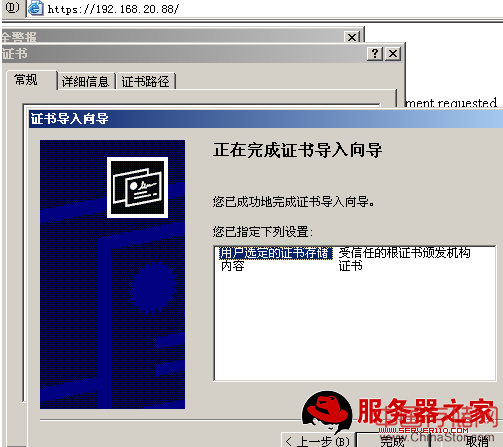
再在客户端打开就有路径了,并将证书安装
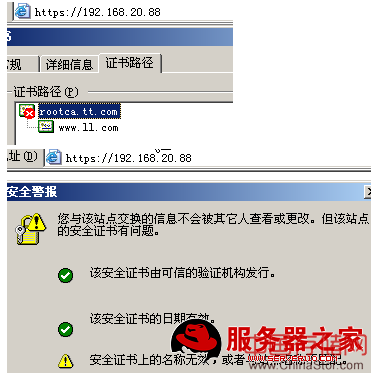
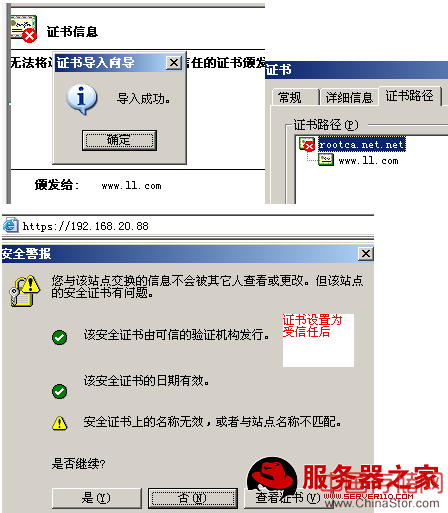
客户端安装证书后,在受信任的根证书办法机构中可以看到
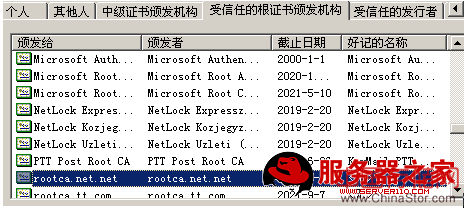
做一下域名的解析后,直接访问域名就不会有证书的安全提示了: